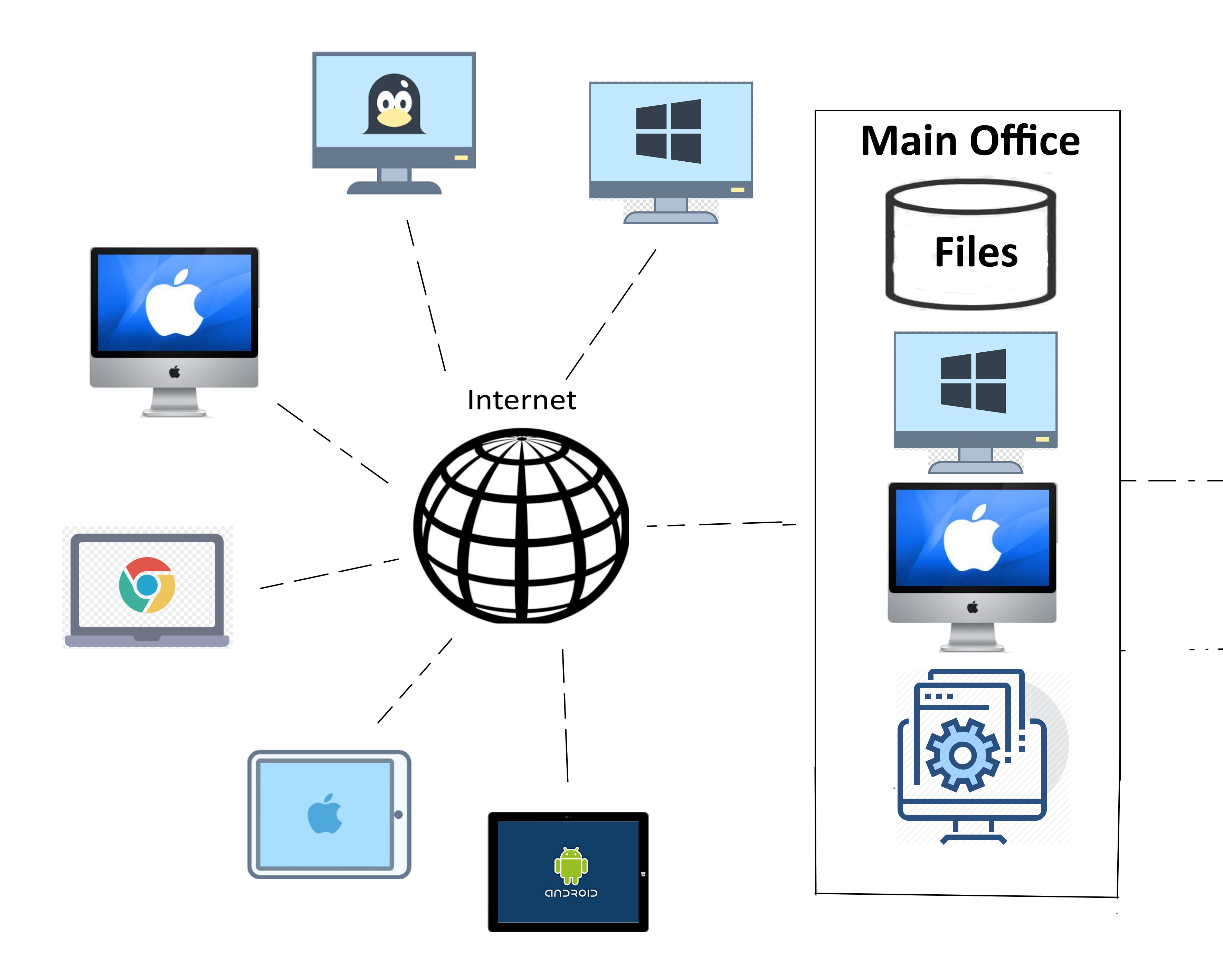
CielView
CielView-Server minimizes redundancy in computing resources while allowing users remote desktop access to virtualized user Desktops. CielView-Desktop provides customized solutions to each user in an organization. Login

It is literally a 'desktop-view' into an individual's workstation that is accessible anywhere in the world where intenet connection is available. Users will have access to their workstations exactly as they left it, and all their applications are available as though they are sitting in front of their desk-top at work. It is HIPAA, SSAE 16, and PCI compliant using Microsoft authentication regime of Kerberos, NTLM and TLS/SSL. Thin-clients for CielView range in sizes as small as a smartphone to a small tablet depending on the user's preference. If you need specially customized thin-clients other than what's widely available in open market, we can build one for you. All user data is on your CVD, including the ones deemed as "local" such as C/D/E drives. Local dirves are always accessible and backed up, therefore a disaster recovery is easily manageable.

CielView operates on various configurations. CielView can be integrated into any type of environment. If you have your IT infrastructure outsourced to a remote data center, CielView can be seamlessly integrated into that type of framework. If your IT infrastructure is in-house, we can integrate CielView into your organization with ease. Administrative access to CielView is remotely accessible from any location by trained CielView engineers. If a user needs help with their CielView-Desktop, such as installing a new software package or changing a configuration, a CielView technician can remotely and easily take control of any CielView-Desktop to solve user's problems. Technical staff is always a phone call or an email away from helping you with any issue.

CielView is designed to leverage idle CPU cycles and other computing resources. CielView is flexible for each person's needs for computational intensity. Our administrative program allows easy configuration to tailor each desktop according to their needs. You can configure your users based on types of tasks, or the departments they belong to, or in any number of different methods that would work for your organization. CielView is designed to work with various types of clients for variety of interfaces such as multiple monitors and HW or SW dongle based software. CielView uses the latest technologies in Hyper-Threading and virtualization, thereby minimizing redundancy to reduce your TCO.
CielView Desktop
CielView Desktop is a Virtualized PC
CielView-Desktop is your "view" into your Operating System that runs your business applications and interfaces with your data. You can have multiple desktops each accessing different subnets within your organization's IT infrastructure. Access to your CielView-Desktop only requires a thin-client and an Internet connection.
Once you have connection to our CielView, and logged into your CVD, it is as though you have full access to your regular machine at your desk in your office, without the headache and cost of maintaining and upgrading actual machines in your office. CielView-Desktop even works in your existing PC running an outdated operating system.
CielView-Desktop runs on any of your hand held devices such as your smartphone or tablets. When the time comes to replace your existing PCs due to hardware failures, you do not have to buy a completely new machine, instead replace them with any number of these much more economical thin-client options.
Business desktop anywhere
Access your business desktop anywhere. CielView desktop is about freedom; freedom to work from anywhere and any place. With CielView Desktop, your workstation, with all your apps and data, are available wherever you have an internet connection no matter what time it.
Thin Clients
We have a full line of thin clients to meet your cloud computing needs. Our thin clients have no moving parts that are prone to wear and tear. Our thin clients produce very little heat and consume less power than your cell phone.
IT infrastructure cost reduction
CielView reduces IT costs. CielView reduces hardware costs of replacing workstation. CielView also reduces server support costs. CielView makes use of idle CPU power in your IT infrastructure.
Efficient desktop support and management
CielView makes managing your PCs and servers simple. CielView Desktops and Servers are remotely controlled. CielView makes creating and setting up CielView Desktops and Servers simple. CielView makes it easy to roll out.
Zloader Malware Exploits Microsoft Digital Signature Verification
Hackers are using Microsoft's digital signature verification to steal user credentials and other sensitive information by delivering the ZLoader malware. Zloader was previously used to distribute Ryuk and Conti ransomware. Researchers at Check Point Research found that Malsmoke, a hacking group, has been using Microsoft's digital signature to distribute Zloader since November 2021. The group already has over 2,000 victims in 111 countries in the United States, Canada and India. ...
December's Patch Tuesday Updates Fixes Seven Security Vulnerabilities
Microsoft has fixed a zero-day vulnerability that is used to deliver Emotet, Trickbot through fake applications. The patch is part of Microsoft's December Patch Tuesday update, which included 67 fixes for security vulnerabilities. The patches cover almost the full portfolio of Microsoft including Edge, Microsoft Office, SharePoint Server, PowerShell, Remote Desktop Client, Windows Hyper-V, Windows Mobile Device Management, Windows Remote Access Connection Manager, TCP/IP, and the Windows Update ...
A Temporary Fix Issued For HiveNightmare / SeriousSAM
A security vulnerability could allow hackers to steal data and allow local privilege escalation according to researcher Abdelhamid Naceri. The issue was originally in October 2020. The issue, CVE-2021-24084, has yet to get an official fix. A micropatch has been rolled out as a stop-gap measure. ...
Another Intel Chip Flaw Exposes Encryption Keys
According to Positive Technologies, a Russian cybersecurity firm, a security vulnerability in Intel chips allow encrypted file access. The flaw also gives hackers the ability to bypass copyright protection for digital content. Positive Technologies found that the vulnerability ( CVE-2021-0146 ) is caused by a debugging functionality with excessive privileges. According to Intel, the flaw allows activation of test o ...
Turn your Raspberry Pi into a print server
According to WIkipedia's Internet Printing Protocol, Internet Printing Protocol ( IPP ) is a specialized Internet protocol for communication between client device and printers or print servers[2]. IPP uses HTTP as its transport protocol. Each IPP request is a HTTP POST with a binary IPP message and print file, if any, in the request message body. The corresponding IPP response is returned in the POST response. HTTP connections can be unencrypted, upgraded to TLS encryptio ...
Using Raspberry Pi as Thin Client
A thin client, or lean client, is a type of computer that relies entirely on its network connection to accomplish tasks. A typical laptop or desktop PC—otherwise known as a fat client—has the memory, storage, and computing power to run applications and perform computing tasks on its own. A thin client, on the other hand, functions like a tv; it only needs to draw the screen and render the sound. The actual computing power residing on a networked host ( or server ). The hosts may be on-site ...
Installing WordPress on Raspberry Pi
In this article, we will be showing you how to set up a WordPress server. According to W3Techs, WordPress powers over 40% of all the websites on the Internet[1]. More than one in three websites that you visit are likely powered by WordPress. For CMS, or content management systems, almost every 2 out of 3 CMS websites uses WordPress[2]. In order to install WordPress, you need a web server stack. In this article, we will go through setting up ...
Set UP Static IP
A static IP address, or fixed IP address, is an IP address that never changes. Not everyone needs a static IP address. Static IP addresses are necessary for devices that need constant access. For example, a static IP address is necessary if your computer is configured as a server, such as an FTP server or web server. If the server was assigned a dynamic IP address, it would change occasionally, preventing your router from knowing which computer on the network is the server. In this article, ...