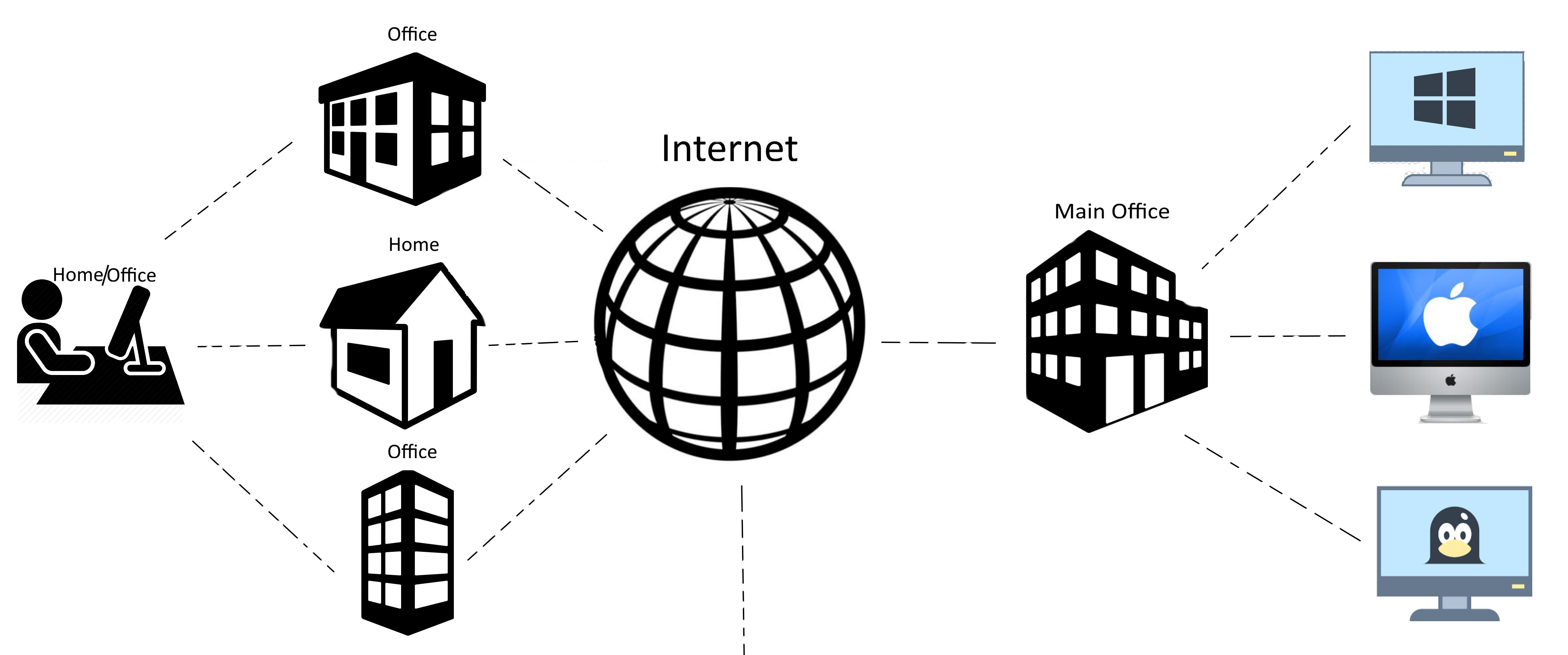
Remote Access
Employees need an equally safe and secure
way to connect to their business's computer and devices from remote locations outside the office.
Login
Login
Overview
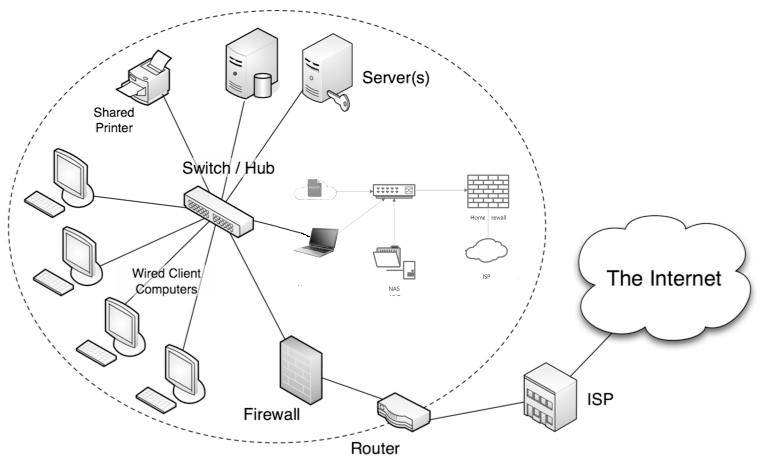
On demand remote access to your:
- office network
- network printers
- network software and local PC software
- files, documents, pictures
On Demand Access
- Remote access your accounting data, files and documents.
- Quickly access your computer desktop as if you are in front of it.
- Full monitoring and managing your office PCs.
- Remotely sharing and collaborating on your office PCs.
Security
ritaShare Box includes ability to block harmful outside contents reaching inside your office network. Enhance resistance against Distributed Denial of Service (DDoS) Attacks from outside sources trying to hamper your network resources.
Gaming Servers
Avid gamers, can build and create custom Game Servers with in their own network. Play an online games with your friends by allowing your friends to join your customized Gaming Server. Share access to customized web-server running your personalized websites. Save tons of money by hosting your own personal websites without paying a monthly fee to web-hosting companies such as godaddy or squarespace.
Turn your Raspberry Pi into a print server
According to WIkipedia's Internet Printing Protocol, Internet Printing Protocol ( IPP ) is a specialized Internet protocol for communication between client device and printers or print servers[2]. IPP uses HTTP as its transport protocol. Each IPP request is a HTTP POST with a binary IPP message and print file, if any, in the request message body. The corresponding IPP response is returned in the POST response. HTTP connections can be unencrypted, upgraded to TLS encryptio ...
Using Raspberry Pi as Thin Client
A thin client, or lean client, is a type of computer that relies entirely on its network connection to accomplish tasks. A typical laptop or desktop PC—otherwise known as a fat client—has the memory, storage, and computing power to run applications and perform computing tasks on its own. A thin client, on the other hand, functions like a tv; it only needs to draw the screen and render the sound. The actual computing power residing on a networked host ( or server ). The hosts may be on-site ...
Installing WordPress on Raspberry Pi
In this article, we will be showing you how to set up a WordPress server. According to W3Techs, WordPress powers over 40% of all the websites on the Internet[1]. More than one in three websites that you visit are likely powered by WordPress. For CMS, or content management systems, almost every 2 out of 3 CMS websites uses WordPress[2]. In order to install WordPress, you need a web server stack. In this article, we will go through setting up ...
Set UP Static IP
A static IP address, or fixed IP address, is an IP address that never changes. Not everyone needs a static IP address. Static IP addresses are necessary for devices that need constant access. For example, a static IP address is necessary if your computer is configured as a server, such as an FTP server or web server. If the server was assigned a dynamic IP address, it would change occasionally, preventing your router from knowing which computer on the network is the server. In this article, ...
