Popular Services
Solution For Small Business
-
Software Installation
We provide fast and professional software installation and upgrade services to keep your systems
up-to-date, secure, and running smoothly. Our experts ensure every update and
installation is done efficiently, enhancing performance and minimizing downtime for homes and businesses alike.
-
Digital Billboard
Turn every empty wall into your best salesperson with easy-to-use digital displays.
Whether it’s a bright screen in your storefront catching the eye of people walking by,
or a friendly board in your waiting room sharing today’s specials, digital signs do the talking for you.
-
Invoice
We create professional, easy-to-use custom invoices tailored to your business needs.
Our solutions simplify billing, improve record-keeping, and help you
get paid faster with a polished, personalized touch.
-
Accounting
We provide professional accounting services to manage your finances accurately,
streamline bookkeeping, and ensure compliance, helping your business stay organized and profitable.
-
Contact Management
We help you organize, track, and manage all your contacts efficiently,
ensuring seamless communication and stronger relationships for your business.
-
Configuration
We provide expert configuration services to set up your systems, software,
and networks for optimal performance and reliability.
-
Software Installation and Upgradation
We provide fast and professional software installation and upgradation services to keep your systems
up-to-date, secure, and running smoothly. Our experts ensure every update and
installation is done efficiently, enhancing performance and minimizing downtime for homes and businesses alike. -
Invoice
We create professional, easy-to-use custom invoices tailored to your business needs.
Our solutions simplify billing, improve record-keeping, and help you
get paid faster with a polished, personalized touch. -
Accounting
We provide professional accounting services to manage your finances accurately,
streamline bookkeeping, and ensure compliance, helping your business stay organized and profitable. -
Contact Management
We help you organize, track, and manage all your contacts efficiently,
ensuring seamless communication and stronger relationships for your business. -
Configuration
We provide expert configuration services to set up your systems, software,
and networks for optimal performance and reliability.
Testimonial
Reviews
Trusted by clients for responsive services, technical expertise, and long-term results.





Excellent rating
Based on 74 reviewsTrustindex verifies that the original source of the review is Google. I found expert computer support and genuine kindness at this service center. When I walked in with a few issues affecting my small business, I was worried they couldn’t be resolved. However, the team quickly helped me tackle all my concerns and more. It’s incredibly reassuring to receive real human tech support from a local provider rather than dealing with someone over the phone or in a chatbot. Their reasonable prices and fast turnaround on expert repairs will definitely keep me coming back. Thank you, Solomon, and your great team!Trustindex verifies that the original source of the review is Google. Excellent service and top-notch knowledge of computer technology. Highly recommended.Trustindex verifies that the original source of the review is Google. They were able to load Windows 11 on my computer and checked it out to make sure no problems. They also spent time trying to find document that disappeared. Very reasonable as well. Highly recommend.Trustindex verifies that the original source of the review is Google. Service was great efficient and quickTrustindex verifies that the original source of the review is Google. They are the best. They Help us out of a big jam, with a same day service. I visit 2 other places before them that couldn't help me with my computer. But Salomon took a second look before sending me to get a new computer. He definitely save us. Since it was a work computer we had a lot of valuable information. I would have given them ten stars if I could.Trustindex verifies that the original source of the review is Google. Excellent service, professional people at hand...Trustindex verifies that the original source of the review is Google. The inputs to my 5 year old pc were not connecting properly. I dropped it off on a Saturday afternoon and was told it would be ready by Wednesday after 5:00. The part they needed arrived and it was fixed and picked up by Tuesday. I would highly recommend Ames Computer and Walden Systems and would absolutely return for future issues if needed.Trustindex verifies that the original source of the review is Google. ...excellent service....Solomon is quite knowledgeable; respectful of your needs and considerate your budget . I have engaged this service on numerous occasions and my tech issues were always resolved in a courteous and professional manner...you can expect updates of progress and clear explanations of the issues ..Trustindex verifies that the original source of the review is Google. Solomon is the BEST!! I've had issues with many machines and no matter what the problem was he fixed them. If you have any problems he can fix it. I've been going to him for a very long time and have been very satisfied every time.Trustindex verifies that the original source of the review is Google. Great service for my Mac desktop! Friendly and fast customer service, highly recommend

Proin tortor mauris, consectetur sit amet faucibus mattis, pretium ac felis. Vestibulum
Al Mahmud
UI- Designer

Proin tortor mauris, consectetur sit amet faucibus mattis, pretium ac felis. Vestibulum
Al Mahmud
UI- Designer

Proin tortor mauris, consectetur sit amet faucibus mattis, pretium ac felis. Vestibulum
Al Mahmud
UI- Designer

32+
Years Expereince
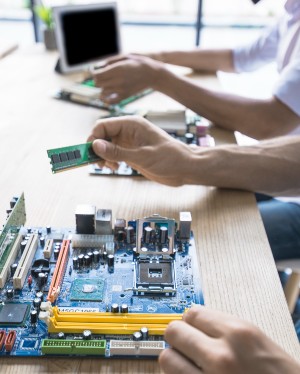
Ames Computer
We integrate current tools with updated software
Ames Computer specializes in customized hardware and appliances. As well as creating innovative enterprise apps for our corporate clients.

Hardware and Software Updates

Programing & Enterprise Apps
- Lorem ipsum dolor sit amet, consectetur adipiscing elit
- Ut enim ad minim veniam, quis nostrud exercitation
- Lorem ipsum dolor sit amet, consectetur adipiscing elit

Michel Foucault
Founder CEO
Dale Earnhards
Reliable experts for fast, professional tech support
Our experts offer prompt, knowledgeable assistance whenever things go sideways. We specialize in solving problems efficiently and professionally, so you can get back to what matters.
Hardware Repair Services
Software Installation
Network Setup
IT Services
Data Recovery
Cybersecurity Services
*Please use the navigation pannel at bottom right for Map controls. Use arrows to naviage, + to zoom in – to zoom out.
Get In Touch
Our Articles
Our latest Articles & News
How to Add Your Company Website in Sage 50 Accounting Sage 50…
How to Add a Company Website in QuickBooks Online QuickBooks is one…
How to Add Your Company Website in Sage 50 Accounting Sage 50…
How to Restore Data from a Windows 7 Backup and Restore Image…



